Few months back I presented a way to block Amazon Fire TV auto update by adding the AFTV update domains to the routers block list. I noticed that this did not stop FireTV auto update, the last time. Others have wrote to me confirming this. With the impending release of Amazon Fire OS 5, which has been found to interfere with Llama and Kodi, it is even more important to block Amazon Fire TV auto update. This post will show you how to block AFTV update on both unrooted Fire TV and Fire TV Stick.
New to Amazon Fire TV and Kodi? Check out: Beginner Blueprint: Complete Amazon Fire TV Kodi Guide. It covers everything you need to know on Amazon Fire TV Kodi setup.
One of the main reasons Amazon Fire TV and Fire TV Stick has been selling like hot cakes is because of its ability run Kodi. Running Kodi directly interferes with Amazon's purpose of selling Fire TVs - to play content from Amazon Ecosystem. While Amazon may never disable sideloading apps, its move to make running Kodi difficult is not surprising. Without further ado, let us see another method to stop Amazon Fire TV from autoupdating. I am currently using my first AFTV update block method and this one concurrently.
Update (Oct 5, 2015): This method is confirmed to work on both Fire TV and Fire TV 4K UHD.
Table of Contents
Block Amazon Fire TV Auto Update
The first way to stop Amazon Fire TV update involved adding the following 3 domains to blocked list on your router administration page.
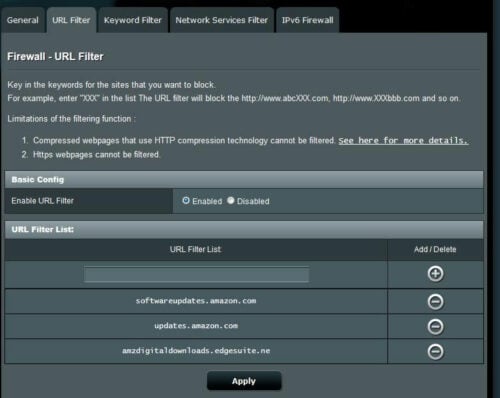
Some have reported that this method does not work on HTTPS domains, which could be the reason for my Fire TV continuing to auto update. The second method described in this post involves using DNSMasq feature in routers. Most advanced routers or routers running open-source firmware such as DD-WRT, Open WRT, Asus-WRT, etc. should allow adding DNSMasqs. [Read: Enhance your Router with a DD-WRT Firmware Upgrade]
In this demo, I am using ASUS RT-AC68U with Merlin's firmware. While the method of adding DNSMasqs may vary slightly with router make and software, the principle still remains the same.
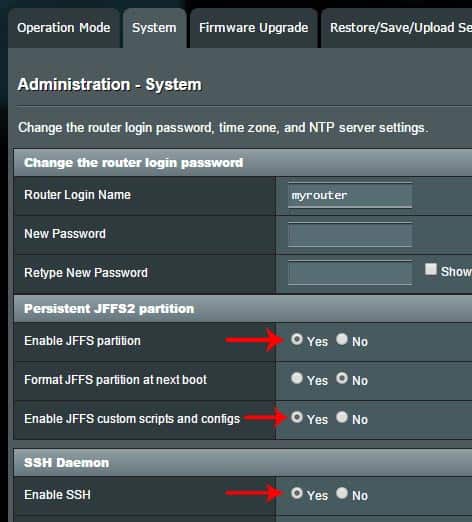
Step 1: Enable JFFS partition and SSH
With some router firmwares, JFFS partition is enabled by default. If not, enable it. Similar, enable SSH access to your router and note down the SSH port (default 22). Below is a screenshot of how to accomplish this in ASUS WRT firmware.
Step 2: SSH into your router
Next, to block Amazon Fire TV auto update, login into your router using SSH. On Windows, you may install PuTTY in case you don't have an SSH client. On Mac or Linux you just open terminal and type in:
ssh [email protected]
Of course, replace USERNAME with your router login username.
Step 3: Add DNSMasqs
Once you are in, navigate to /jffs/configs folder. If it does not exist, create a file called dnsmasq.conf.add (notice that the file name is dnsmasq.conf.add and not dnsmasq.conf):
vi dnsmasq.conf.add
First press a and copy-paste the following lines to it:
address=/amzdigitaldownloads.edgesuite.net/127.0.0.1 address=/softwareupdates.amazon.com/127.0.0.1 address=/updates.amazon.com/127.0.0.1 address=/a1910.d.akamai.net/127.0.0.1 address=/softwareupdates.amazon.com/127.0.0.1 address=/firs-ta-g7g.amazon.com/127.0.0.1 address=/amzdigital-a.akamaihd.net/127.0.0.1
Update (Apr 5, 2016): Added amzdigital-a.akamaihd.net to address change of domain in Fire OS v5.0.5.1.
Update (Oct 14, 2014): Removed atv-ext.amazon.com per Terry's comment below.
Save and exit by pressing Esc, wq, and Enter in sequence (or learn how to use VI editor). These DNSMasq rules will stop FireTV autoupdate by blocking access to Amazon software update domains. Finally, reboot your dnsmasq service for the rules to take effect.
service restart_dnsmasq
Alternatively, you may just reboot the router. After reboot, SSH into your router again and open /etc/dnsmasq.conf file. Scroll down and ensure that the lines you added to dnsmasq.conf.add file are present here. The picture below shows an example.
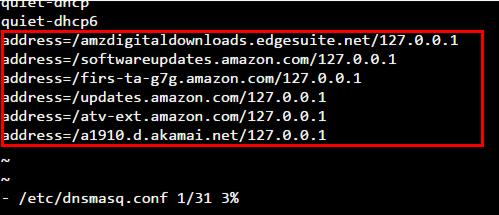
That is it, you all set. Your router should now block new Fire TV update (hopefully, you never know when Amazon may change its update method). Blocking Fire TV auto update also protects your root as well as running launchers such as FireStarter. In fact, there are reports that the Fire OS 5 blocks FireStarter. So go ahead, block Amazon Fire TV auto update and preserve the hard work you have put in so far.





![Top-5 Best AdGuard Home Configuration Tips [2022] AdGuard Home Banner](https://www.smarthomebeginner.com/images/2022/04/AGH-toptips.webp)
![10 Best Jellyfin Client Devices [2022] - 4k, Hardware Transcoding, etc. Jellyfin Roku App](https://www.smarthomebeginner.com/images/2021/02/jellyfin-roku-client-app-ft.jpg)